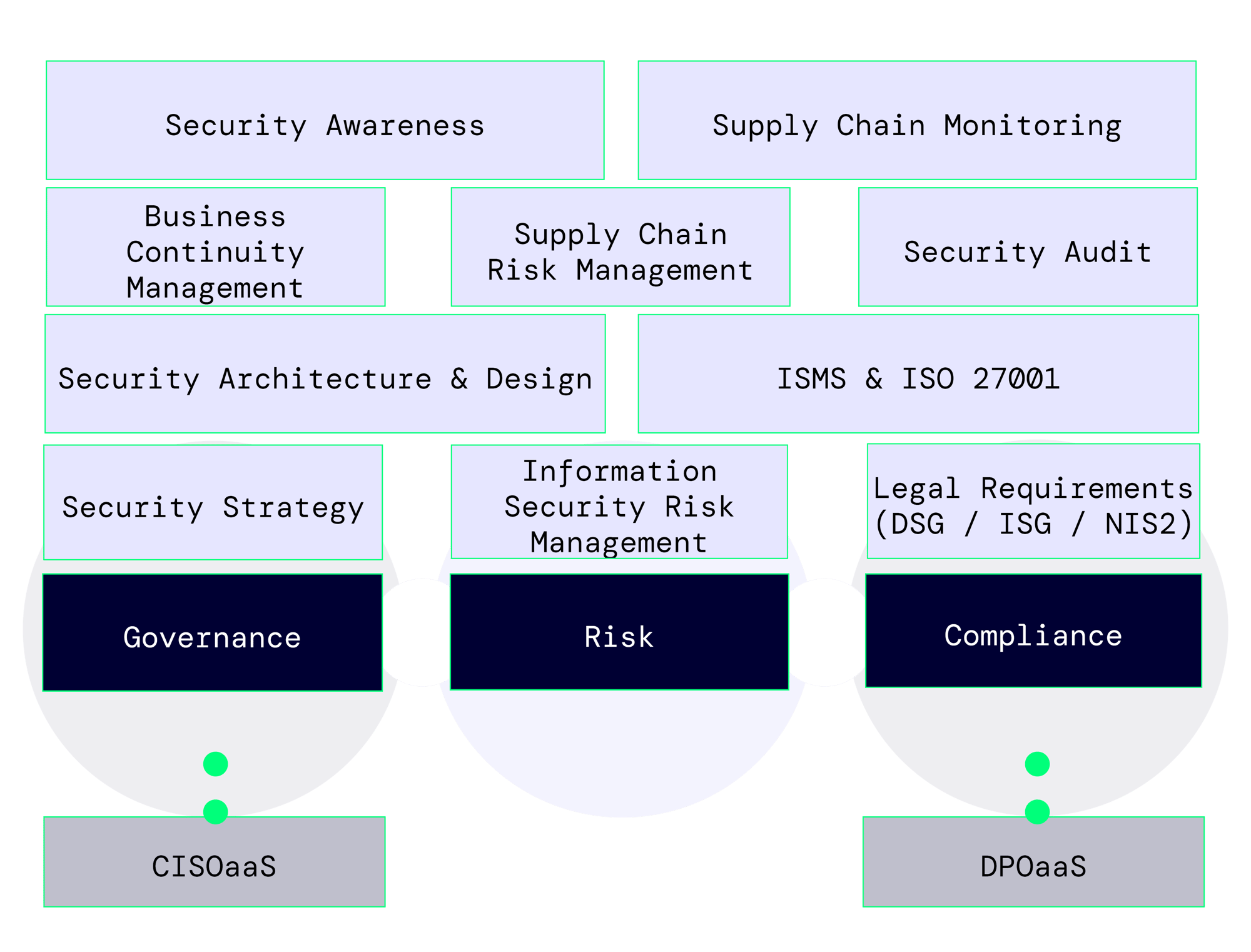
Governance, Risk, Compliance
Whitepaper: Building Resilience with the Right Strategy: Setting Up IT Security Effectively
A guide to creating lasting security
Read now
Efficient Measures for Low-Risk and Compliant Corporate Governance
BNC is your trusted partner in Governance, Risk, and Compliance (GRC). Our team of experts is dedicated to ensuring that your organization meets all legal requirements while maintaining a robust security posture.
You will benefit from a customized Information Security Management System (ISMS) that is specifically designed to meet the unique needs of your organization—no generic templates involved.
We provide close support to stakeholders to ensure that the functioning and interconnections within the ISMS are understood by all parties involved.
We speak both GRC and IT engineering languages.
We integrate security awareness measures into the implementation to address the relevant risks for the organization.
Establishing an Effective and Efficient Security Risk Management System
Establishing an effective security risk management system is crucial for protecting your organization. Depending on your organization's structure and resources, there are various approaches, such as a centralized focus on potential risk scenarios or an asset-centered approach that targets specific information assets.
At BNC, we adopt an integrated approach that flexibly adapts to new threats and is regularly reviewed. This ensures that your risk management remains a dynamic tool for continuous improvement.
Risk Assessment and Business Continuity Management
Ensuring the sustainability of your organization in adverse circumstances requires the correct selection of criteria for risk assessment and risk acceptance within your risk management framework. This selection leads to effective measures for risk treatment. For residual risks and unexpected events, we develop business continuity plans tailored to various extreme scenarios. Regular testing and exercises validate these plans, ensuring that your organization is prepared for as many eventualities as possible.
We provide an auditor’s perspective, ensuring you have both the essential documentation and the right answers for a successful ISO 27001 certification.
We bring practical expertise gained from a wide range of IT projects.
Together, we create pragmatic solutions to implement effective security measures that deliver results.
Our goal is to achieve sustainable improvements in your organization's security that extend beyond merely obtaining certification.
Relevant Scenarios in Business Continuity Management
A robust Business Continuity Management (BCM) system must offer practical methods for a variety of scenarios without becoming overly abstract. At BNC, we focus on specific risks such as IT system failures, cyberattacks, destruction of critical infrastructure, and site-related challenges. By planning and establishing emergency committees along with their defined authorities, we ensure that your organization remains operational even in unforeseen situations.
Ensuring Security in the Supply Chain
Ensuring security in the supply chain is a critical component of an Information Security Management System (ISMS) and is vital for the overall security of your organization as well as compliance with data protection regulations. There are various methods to evaluate suppliers, ranging from reviewing certifications like ISO 27001 and ISO 9001 to utilizing detailed self-assessment questionnaires and conducting comprehensive audits. The appropriate approach depends on the supplier's role in your security framework and its relevance to your business processes.
Our consultants assist you in developing an effective supplier management strategy tailored to your organization’s needs and train your employees to conduct regular and qualified evaluations of suppliers.
Blog: Data Breach - Trusting Partners Has Become More Than A Human Matter
How ISO/IEC 27001:2022 Supports Companies, Builds Trust, and Establishes Their Reputation as Trusted Players
Read now!
Efficiently Demonstrating Compliance Requirements
Efficiently demonstrating compliance with increasing regulatory demands, such as DSG, GDPR, ISG, and NIS-2, can be challenging. BNC supports you by centralizing these requirements within an Information Security Management System (ISMS), thereby minimizing redundant work and enabling efficient reporting. This approach reduces the effort needed to meet regulatory obligations and keeps documentation for partners and suppliers manageable.
Conclusion: BNC’s Support in Governance, Risk Management, and Compliance (GRC)
BNC’s certified experts develop tailored solutions and collaborate closely with your stakeholders to implement an effective Governance, Risk Management, and Compliance (GRC) system.
By conducting targeted risk assessments and ensuring adherence to data protection regulations, we enhance your organization’s security posture and optimize compliance processes. With BNC as your partner, you can reduce the effort required for regulatory compliance while streamlining documentation for partners and suppliers.
Whitepaper: Third-Party Risk Managament
Discover Our Expert Strategies to Mitigate Hidden Threats and Safeguard Your Future Success
Download now for free!
FAQ Governance, Risk, Compliance (GRC)
-
There are so many topics in the GRC (Governance, Risk, and Compliance) field; which ones should we start with?
To improve governance and achieve compliance, a risk-based approach is usually the most effective strategy. This allows the existing budget to be invested where the highest risks have been identified, effectively reducing the security risk. The goal is not to eliminate risks entirely, but to reduce them to an acceptable level.
-
How does BNC support a quick recovery after a ransomware attack?
To strengthen the resilience of your organization, BNC offers a combination of measures that directly and indirectly support Business Continuity Management.
For a rapid recovery of operational activities after a major security incident, a functioning emergency and recovery plan is essential, which we will help you create based on practical experience.
Furthermore, this plan should be regularly tested through practical exercises, for which we can offer a wide range of options, from real recovery tests to customized tabletop exercises.
Last but not least, we can prepare all employees for emergencies with security awareness measures, thereby simplifying communication within the organization and significantly reducing the time needed to resume business operations after an incident.
If these measures are insufficient, we also offer an Incident Retainer Service in addition to consulting, so that experienced coordinators and analysts can assist you promptly during emergencies and guide you through the emergency process.
-
Which standards and regulations can BNC assist us with in achieving and maintaining compliance?
The BNC Cyber Security Consulting Team regularly undergoes further training and expands its portfolio according to customer needs. Currently, we can provide experience and certifications for the following standards and regulations:
- ISO/IEC 27001
- ISO/IEC 27005
- TISAX
- New Swiss Data Protection Act and the European GDPR / DSGVO
- The Swiss Information Security Act and the European NIS-2
- ICT Basic Protection for the Federal Administration
-
What is the difference between ISO 9001 and ISO 27001?
ISO 9001 focuses on the Quality Management System (QMS) and requires suitable processes and controls to ensure consistent quality of services and products.
ISO 27001 describes the establishment and operation of an Information Security Management System (ISMS), which helps improve the confidentiality, integrity, and availability of your data and systems.
These two standards can be implemented independently, but they complement each other well and can be integrated into a combined management system.
-
Why have we been receiving regular questionnaires about our security measures from our business customers lately?
These are likely measures your customers have implemented to assess the security of their supply chain. The NIS-2 regulations and the Data Protection Act require specific, recurring actions to control and reduce risks across the entire supply chain. Due to these legal requirements, many industries and all organizations within critical infrastructure must maintain a management system for third-party management.
BNC can help you integrate and maintain this third-party management within your ISMS.
